
Harden Your Defenses With Security Analytics
Analyze data in real time with the right SIEM approach. It's time to step up your security game. If you...

5 ways to reduce risk with continuous monitoring
The rise in breaches over the past few years has made it clear that many organizations are overwhelmed...
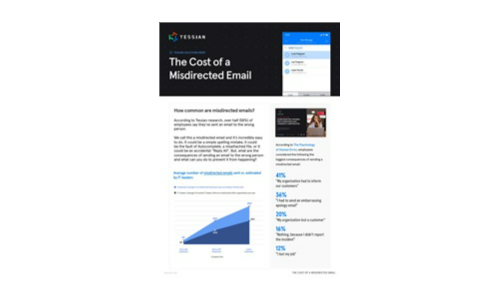
What is the Cost of a Misdirected Email?
The average number of misdirected emails is almost always higher than IT leaders estimate, making it...

Reinventing work in development teams
Software engineering teams were often among the best placed to adjust to 2020's shift to working from...

Wealth Management: Driving Transformation Through A 360° Client Lens
A 360-degree customer view is fast becoming essential for financial organisations and wealth managers...

The Digital-first Toolkit
Over the past year, society has proven we can be effective, creative and productive working from anywhere—even...

Reimagine How Work Gets Done - Introducing Fujitsu Work Life Shift
It's time to reimagine a new future. The concept of the workplace has changed forever. It's no longer...

IT and Cyber Incident Response Communication Templates
BlackBerry® Alert is a critical event management (CEM) solution designed to help organizations prepare...

10 Reasons to Adopt E-Signature
The way we work has changed. Modern organisations are putting together new technology systems that allow...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




