
The Power Of Personalization
Back in the day, brands' communications to their customers used to consist of a memorable message delivered...

Cyberthreats: A 20-Year Retrospective
Annual threat reports provide an opportunity to look back at significant events of the past 12 months...

5 Steps For Introducing Audit Software Into Your Organization
In addition to their cyclical audits of specific financial and operational areas, today's internal audit...
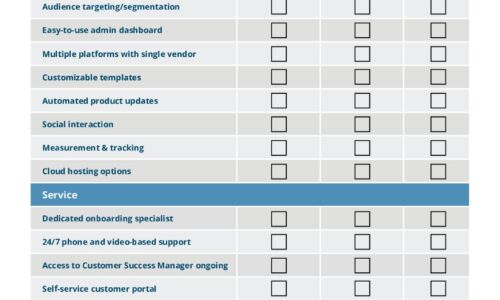
IT Comms Plan Bundle
IT teams need to communicate important messages across their organization – from scheduled maintenance...

Find and Protect your sensitive Data with SQL Server Complance tools
This technical brief examines a database compliance and security scenario in the enterprise. It describes...

Part Five - Futureproofing your cybersecurity strategy
Payment fraud occurs when a thief steals someone's payment information to make unauthorized transactions...

Common Browser Isolation challenges, and how to overcome them
A growing number of security teams are implementing a Zero Trust security strategy, in which no application,...

How to Create a Successful Cybersecurity Plan
Along the edge of subway tracks in the UK is a sign that says, 'Mind the gap,' warning passengers to...

Web Coding and Development All-in-One For Dummies
Speak the languages that power the web. With more high-paying web development jobs opening every day,...

Nasuni for Rapid Ransomware Recovery
The FBI's Cyber Crime division defines ransomware as 'an insidious type of malware that encrypts, or...

Instant data for real-time business results
Machine learning is evolving faster than ever – AI and analytics can give you the capabilities to become...

2020 Customer Experience (CX) Transformation Benchmark
During the pandemic, consumers are turning to customer service more than ever, thus it has become an...

GigaOm Radar for DDoS Protection
Cloudflare ranked higher than any other assessed vendor and is named a 'Leader' and 'Fast-mover'' in...

Cloud Security Generation Z
Also known as the 'Cloud Generation,' this Generation Z is already reshaping IT…and careers. Many are...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.