
2022 State of the Threat: A Year in Review
In 2022, ransomware remained the most prevalent form of attack. In investigations by Secureworks® incident...

Defend Against Ransomware
Defend your organization from evolving ransomware attacks. Learn what it takes to reduce risk and strengthen...

Security Operations Use Case Guide
Responding to security incidents and vulnerabilities is an ongoing process, and you know that reacting...

The Passwordless Future Report
Every company has to become a technology company in order to survive and thrive in today's competitive...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

3 Benefits of Running Your Business-Critical Applications on NetApp
Make the Most of Your Essential Data Today's customers are connected. They want information at their...

Take Control of Security Operations with Consolidation and XDR
The constantly evolving cyber threat landscape and steady stream of cybersecurity technologies designed...

A Guide for SMBs: Can I really become “less hackable”?
After nearly 20 years working in cybersecurity, I am still asked the age-old question by business owners:...
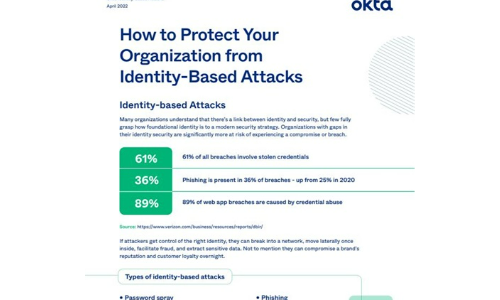
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

2021 Data Risk Report - Manufacturing
Our 2021 Manufacturing Data Risk Report focuses on the growing cybersecurity threats facing industrial...

Unmasking BEC and EAC
Whether they result in fraudulent wire transfers, misdirected payments, diverted payrolls, supply-chain...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


