
Defend Against Ransomware
Defend your organization from evolving ransomware attacks. Learn what it takes to reduce risk and strengthen...

7 Common Ways Ransomware Can Infect Your Organization
Understanding how ransomware infects a device and spreads across a network is crucial to ensuring that...

10 Endpoint Security Problems Solved By The Cloud
Are you experiencing problems with your traditional AV solution? Read the eBook 10 Endpoint Security...

Dell And Partners Workforce Productivity Benefits
Dell and its partners provide a range of solutions that enable their customers to transform the capabilities...

The Data Breach is Coming from Inside the House
Real-Life Tales of Data Loss, Insider Threats and User Compromise Data doesn't lose itself. People lose...

Customer Experience Challenges in Pandemic Times
Delivering great customer experiences (CX) isn't always easy, even in the best of times. When the stakes...

Don't Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

A Guide for SMBs: Can I really become “less hackable”?
After nearly 20 years working in cybersecurity, I am still asked the age-old question by business owners:...
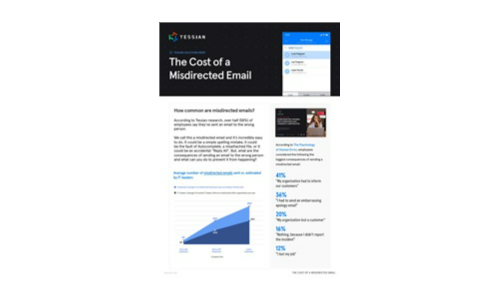
What is the Cost of a Misdirected Email?
The average number of misdirected emails is almost always higher than IT leaders estimate, making it...

The Essential Guide to Managing Laboratory Samples
This three-part guide explores common problems experienced in the management of samples and how, for...

Brilliant Experiences, Channel by Channel
Communicating in ways that speak to each individual customer, is what allows brands to build strong relationships....

The CISO's Guide to Ransomware Prevention
Ransomware attacks have transformed the cyber attack landscape. These sophisticated and persistent threats...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

