Latest Whitepapers
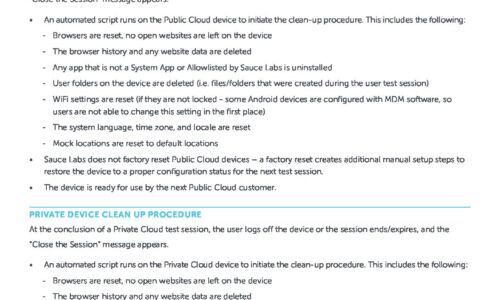
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

Threat Intelligence Critical to Cyber Security Protection
Financial services institutions are at the forefront of cyber-attacks and keeping information safe is...

Powering your organisation with an agile productivity stack
I wonder where our important files have run off to today.' When you've got one seamless, secure platform...

Executive Brief: The Ransoming Of Higher Education
Coordinated attacks are hitting higher education institutions across the nation and around the world....

A guide to the benefits of Unified Communications & Collaboration
In order to succeed, modern businesses must seek to create a workplace that delivers an exceptional customer...

Getting Started with SASE
Secure Access Service Edge: A guide to secure and streamline your network infrastructure As enterprises...

Defend Yourself Against Ransomware and Other Types of Malware
The May 7, 2021, ransomware attack on U.S. fuel network Colonial Pipeline left millions afraid they couldn't...

Take Control of Security Operations with Consolidation and XDR
The constantly evolving cyber threat landscape and steady stream of cybersecurity technologies designed...

IoT Use Cases: Smart Ports
Smart Ports utilize Internet of Things (IoT), Artificial Intelligence (AI), and data to make itself more...

Achieving Operational Excellence in Food and Beverage Manufacturing
Sage Business Cloud Enterprise Management. The environment food and beverage manufacturers operate in...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









