Latest Whitepapers

Four Ransomware Resiliency Challenges You Can Combat with Confidence
Ransomware is a growing thread to operational resiliency in all digital enterprises. These four stories...

Enhanced Privilege Access Management Solutions
Privileged Access Management (PAM) is one of the most important areas of risk management and security...
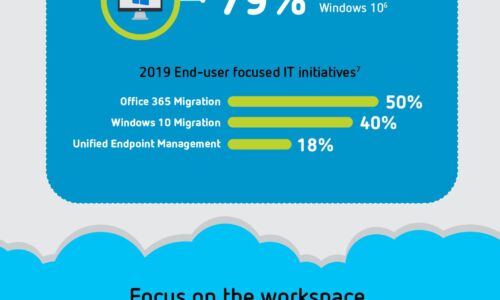
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

A guide to the benefits of Unified Communications and Collaboration
In order to succeed, modern businesses must seek to create a workplace that delivers an exceptional customer...

Understanding Why Multi-Signal MDR Matters
MDR providers can only detect and respond to what they can see. A multi-signal approach is paramount...

The Defender's Advantage Executive Summary
Cyber Defense is one of four closely integrated Information Security domains, tasked to enable organizations...

Public and Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

PerimeterX is named a leader in Bot Management by Forrester
PerimeterX was named a leader in The Forrester New Wave™: Bot Management, Q1 2020. According to the...

Finding Revenue and Profit Growth Opportunities in Retail
In this whitepaper, learn how retailers can drive revenue and profit growth by using new technologies...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









