IT Security

Why Today's Business Applications Belong in the Cloud
Has there been a more exciting time to be at the forefront of business? It's unlikely. According to a...

Driving Real Behaviour Change
Today's most potent cyber threat isn't a zero-day vulnerability, new malware or the latest exploit kit....

Ponemon Report
Ponemon surveyed 1,826 IT professionals globally to understand the state of SD-WAN, SASE and Zero Trust...

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...

A Spec for Success: Building within a Common Data Environment
In the decade since the 2009 economic downturn in the UK, there have been a number of changes in the...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

BIOS Security – The Next Frontier for Endpoint Protection
Everyone is familiar with the process of booting up a computer. Many of us do this every day — pressing...

Report Summary: TLS 1.3 Adoption in the Enterprise
This research project sought to gauge awareness of and adoption plans for the new TLS 1.3 specification...

14 Questions to Ask Your Application Security Vendor
When evaluating application security vendors, you have a great deal to consider. Understanding your goals...
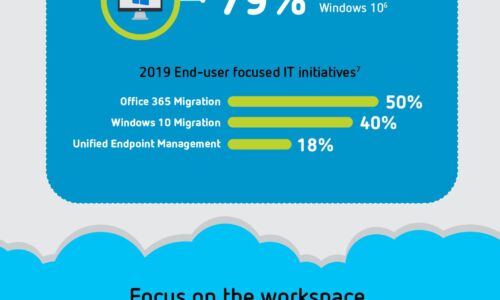
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Ransomware Survival Guide
Be Ready for Ransomware Ransomware is an old threat that just won't go away. While overall volumes have...

Activate ESG Use Case Guide
Incorporating robust ESG practices into business strategy and execution is critical, not only to be a...

The Business Email Compromise Handbook
A Six-Step Plan for Stopping Payment Redirection, Supplier Invoicing Fraud and Gift Card Scams Sometimes,...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.