Compliance

7 Reasons VMware Cloud Foundation is the Premier Hybrid Cloud Solution
Is your IT service delivery future ready? Application and cloud strategies are inextricably linked, and...

Achieving pervasive security above, within and below the OS
It seems that every few months, another prominent global brand experiences a major security breach and...

The Impact of XDR in the Modern SOC
The buzz around extended detection and response (XDR) is building. But there's still a lot to learn about...

Three Steps to Ultimate Cyber Resilience
Security breaches have become a fact of corporate life over the past few years. Cyberattacks are accelerating...

AWS for Healthcare: Accelerating the Future of Personalized Healthcare
For healthcare organizations, the challenge of providing patient centered care amid ever-increasing costs...

What Makes Real Threat Intelligence
First popularized in terminology several years ago, threat intelligence means many things to many people....

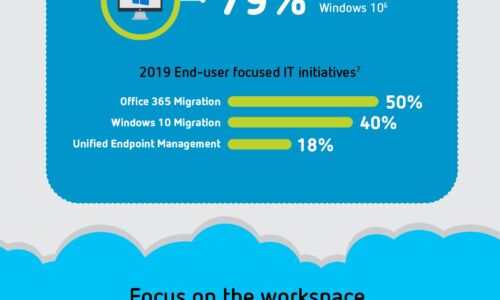
Quest® unified endpoint management
Doing business today requires an increasing number of devices and platforms, making IT endpoint management...

When Networks Meet The New Tomorrow
This paper looks at IT priorities that organizations will need to address now and in the new tomorrow: +...

BNPL Consumer Research Report 2022
Buy Now, Pay Later (BNPL) financing has become hugely popular over the last few years. However, as BNPL...

The 10 Biggest and Boldest Insider Threats of 2019 and 2020
That risk is only increasing in an era of remote working and distributed teams. Without a holistic security...

The Inner Circle Guide to Agent Engagement and Empowerment
Your agents aren't going to ask you for more automated tools, empowered and personalized coaching, and...

University of Surrey's Edification for its Cyber Protection
The University of Surrey is a public research university in Guildford, England, receiving its royal charter...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.