Collaboration

Seven reasons why your enterprise needs intelligent search
Organizations are hungry to use data to grow and improve performance, but enterprises are struggling...

Preparing for the post-pandemic workplace
As enterprises look towards the challenges of a post-pandemic world, one thing is widely acknowledged....

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...

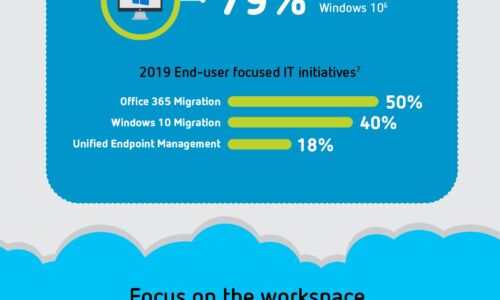
Not All End User Experience Monitoring Solutions Are Created Equal
Digitization has undoubtedly changed the way companies do business with their customers, partners and...

Your Path to Cloud Analytics: 10 Key Considerations
Now more than ever, businesses are choosing SaaS for modern analytics. That's because today's vastly...

Discover How Organizations Speed AI/ML Adoption with Red Hat Openshift
Turn your data into a valuable business asset and a competitive advantage. Artificial intelligence (AI)...

Would you be ready... if you need to open new offices in 10+ countries?
Midsize companies play a key role in the global economy, driving a large share of job creation, economic...

Reinventing customer service
The upheavals of 2020 created an opportunity for customer service teams to rethink service delivery and...

Unlocking Collaboration: Making Software Work Better Together
The recent and rapid pace of change in the workplace has required companies to rethink their tools and...

Solving the Talent Puzzle
The top five percent of professional services organizations (PSOs) are experiencing low levels of attrition,...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.