Android
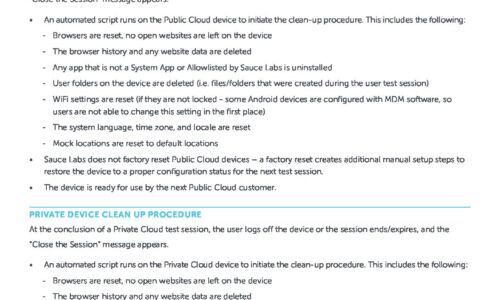
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

It’s 5 Toughest Work from Home Challenges and How To Solve Them
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...

Trusted Access Report
As global conflicts spill into the digital realm, protecting people through to the enterprise is increasingly...

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

Deep Learning For Dummies
Take a deep dive into deep learning Deep learning provides the means for discerning patterns in the data...

The Forrester Wave™: Enterprise Email Security, Q2 2021
In a 25-criterion evaluation of enterprise email security providers, Forrester identified the 15 most...

Enable End-to-End Zero Trust To Achieve Effective Outcomes
Zero Trust priorities have evolved in 2020 to require solutions that secure your remote workforce with...

The World is Your Workplace: Public Safety Mobile Solutions
Public safety personnel of all types rely on mobile technology to remain connected, efficient and informed....

It's 5 Toughest Work from Home Challenges and How To Solve Them
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...

Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...

Taking Public Sector Mobility to the Next Level
A new breed of tablets is powering ultra-mobility. Public sector employees have always been mobile, the...

M1 quick start guide
Apple will soon fully transition all the Macs in its lineup to the new ARM-based M1 chips and mobile...

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
