Android

Time to Replace Laser Scanners: Myth-busting Software Scanning
Last mile operations are complex and challenging. Delivery companies across the globe are increasingly...
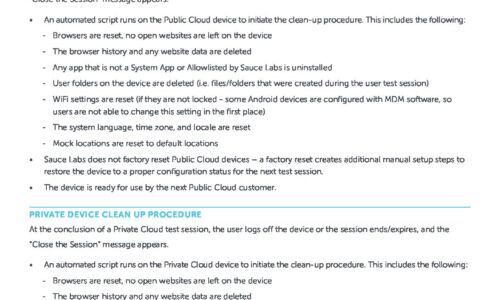
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

Trusted Access Report
As global conflicts spill into the digital realm, protecting people through to the enterprise is increasingly...

IT's 5 Toughest Work from Home Challenges
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...

Push Notifications: What They Are, How They Work, and Why They Matter
Although more than a decade old, push remains innovative and versatile. Initially used by brands to engage...

Forrester Wave, We’re a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

2021 State of the Threat in review
The State of the Threat report is compiled by the world-renowned Secureworks® Counter Threat Unit™...

Functional Programming For Dummies
Using functional programming techniques can make you incredibly efficient when solving certain problems...

Buyer’s guide to all-in-one IT support and management
IT can be hard to manage and support in today's flexible world. Many help desk teams have amassed various...

Designing Hyper-Aware Industrial Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
