Open Source

The Ultimate Guide to Document Processing Automation
Today, there are many different technologies a line of business department or automation COE are able...

Toad for Oracle Tips and Tricks
Toad® for Oracle has been the IT community's tool of choice for more than a decade. With Toad, you are...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...
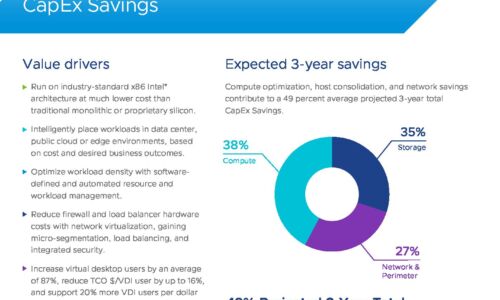
VMware Cloud Foundation: Maximise Digital Business Value
76% of IT organizations are committed to hybrid cloud as a long-term strategy to quickly adapt to changing...

Modernize application delivery with cloud services
The pace of digital transformation is accelerating as businesses adapt to changing customer expectations....

Red Hat for cloud-native development
Application development is a complicated undertaking that requires a complex environment and tools. With...

Advanced Application Threats Require and Advanced WAF
The threat landscape is dramatically different than it was just 5 years ago. A traditional web application...

Top Ways Your Cloud Approach is Burning Cash
Through our work across hundreds of clouds and tens of thousands of containers and workloads, we've captured...

Microsoft Digital Defense Report
Over the past year the world has borne witness to a burgeoning cybercrime economy and the rapid rise...

The Total Economic Impact™ Of Red Hat OpenShift Cloud Services
Modern-day companies are expected to have the capabilities, skills, and tools to support evolving customer...

Penetration Testing For Dummies
Target, test, analyze, and report on security vulnerabilities with pen-testing Pen-Testing is necessary...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


