Network

Understanding cybersecurity workforce problems and solutions in 2021
The findings in this large-format survey reinforce existing statistics and, in certain instances, actually...

Untangling the Web of Cloud Security Threats
Changing technologies and evolving threats make IT security more challenging. Business units are adopting...
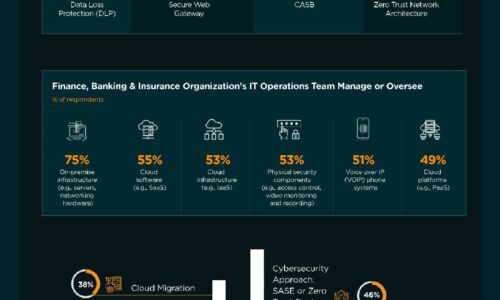
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

GBS on Now - Make work flow across the silos
Today, there is a need to re-imagine the role of delivery structures within the enterprise. A new global...

High Speed Network Encryption
High Speed Encryption (HSE) secures data in transit and data in motion, as it moves across the network...

Cloud Security Generation Z
Also known as the 'Cloud Generation,' this Generation Z is already reshaping IT…and careers. Many are...

Securing DNS by Design
3 Critical Protections from Your DNS Service: How Your Service Provider Can Protect Your Enterprise DNS...

Zero Trust Network Access
VMware Secure Access provides enterprises a way for their employees to leverage a secure and fast connection...

The Best of Both Worlds: Hybrid IAM Offers Flexibility and Enhanced Security
One of the fastest growing segments of the Identity and Access Management (IAM) market is the cloud segment. Increasingly,...

How To Simplify Security With Cybersecurity Mesh Architecture
Networks are becoming increasingly sophisticated and widely distributed, which is making them even more...

Migrating SAP to the Cloud
Transform SAP into the foundation of your competitive differentiation Enterprises such as BP, Bristol-Myers...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


