Mobile Security

Time to Replace Laser Scanners: Myth-busting Software Scanning
Last mile operations are complex and challenging. Delivery companies across the globe are increasingly...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

App Development as a Core Business Capability
Many organisations now understand the critical role that apps play in enabling their people, as well...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...
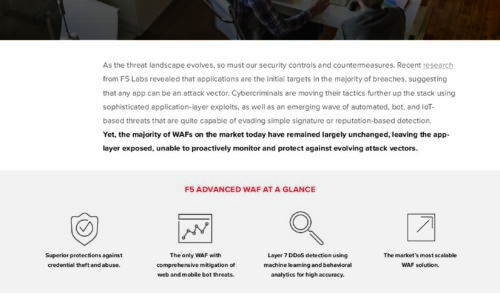
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Which WAF is right for me eBook
Despite the tech industry's collective best efforts to bolster secure application development practices,...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

Enhanced Privilege Access Management Solutions
Privileged Access Management (PAM) is one of the most important areas of risk management and security...

Hidden Costs of Endpoint Security
When it comes to endpoint security, CISOs are in a bind. Most assume that endpoints will be compromised...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.