Mobile Computing

Going Digital For Business Continuity
COVID-19 has created a global reorientation in business operations. Global lockdowns have reprioritized...

Human Factor Report 2021
Cybersecurity, Ransomware and Email Fraud in a Year that Changed the World As the global pandemic upended...

Connected cities and places
Improving digital infrastructure is key to enabling a smarter city or place to develop, thereby creating...

Six Top Trends and Predictions for Data, Analytics, and AI in 2021
Although making predictions about the future is difficult even under the best of circumstances, it's...

Modern Blueprint to Insider Threat Management
Taking a People-Centric Approach to Your Insider Threat Management (ITM) Programme. Insider threats can...

SaaS pricing in uncertain times – 4 things to consider
Software as a Service (SaaS) vendors faces challenges when pricing their services, particularly in the...

Refresh your thinking: You've got a platform problem
The pressure on IT is mounting. Can you meet it before it becomes too great for today's systems and processes?...

Python All-In-One For Dummies
Your one-stop resource on all things Python! Thanks to its flexibility, Python has grown to become one...

Redefining Modern Enterprise Storage for Mission-critical Workloads
The digital business demands being placed on enterprise-scale IT organizations are now so extreme that...
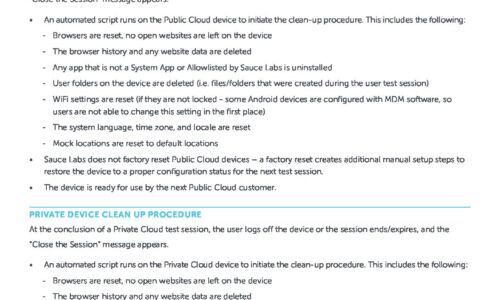
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

Dell Technologies Continuously Modern Storage
IT's role in business has changed. IT organizations were traditionally once viewed as cost centres, but...

Digital Transformation & Risk for dummies
Digital transformation is a critical priority for many companies across most industries, and it's more...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

