IT Security

A Zombie's Survival Guide in a Changing Database World
With the rise of autonomous databases – and all the other scary changes in database management systems...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

5 Reasons to Upgrade Your Symantec Email to Proofpoint
Symantec is now part of Broadcom, a semiconductor manufacturing company. For Symantec customers of all...

How 3 Leading Companies Found Peace of Mind with Disaster Recovery
Many traditional DR solutions are unreliable, complex and expensive, requiring significant and time-consuming...

The Economics of Cloud Options in Healthcare
Through the lens of Cloud Economics, explore the risks and benefits of the three ways to upgrade and...

Ponemon Cost of Insider Threats Report 2022
External attackers aren't the only threats modern organisations need to consider in their cybersecurity...

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

The Business Value of Storage Solutions from Dell Technologies
In the era of digital transformation — the evolution toward much more data-centric business models...
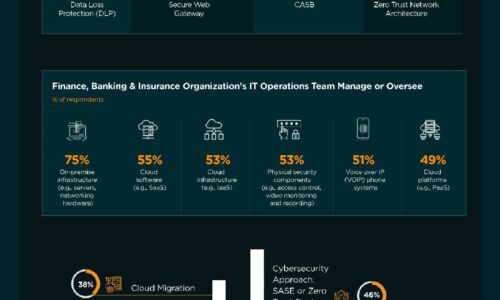
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Activate ESG Use Case Guide
Incorporating robust ESG practices into business strategy and execution is critical, not only to be a...

Unlock the Power of Hybrid Cloud with Consistent Operations eBook
Embracing a hybrid cloud operating model creates new possibilities for IT organizations, paving the way...

Fortinet Security Solutions for SAP S/4HANA
With today's challenges and economic climate, organizations leverage enterprise resource planning (ERP)...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

