IT Management

Your Data. Their Cloud.
In today's organizations, digital transformation is a vital imperative—and cloud services offer a proven...
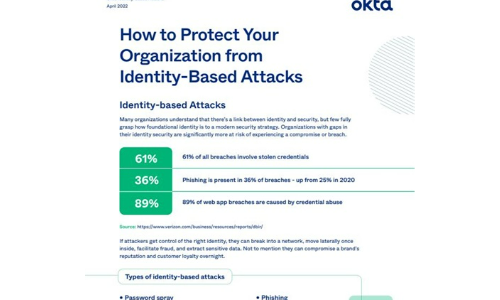
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Managing Sprawl in Microsoft 365
How content sprawl happens, why it matters, and steps every IT leader should take to avoid it. Sprawl...

Healthcare IoT, the RX for Providers and Patients
Healthcare providers have a lot on their plates. Costs are always on the rise, and staff shortages put...

Find new growth opportunities with business model innovation
The world is changing faster than ever, but new opportunities mean that now is the time for your business...

Intelligent technology for media workflows
Technology in media evolves quickly. Once seen as buzzwords, AI and machine learning (ML) are now crucial...

Migrating Enterprise Applications to Microsoft Azure
Migrating applications is a subject that can strike fear into the heart of even the most seasoned IT...

6 Steps to Implementing a Zero Trust Model
An all or nothing approach to Zero Trust is a tall task. What if you took a more incremental, agile approach...

A More Effective CIO-CFO Partnership
How are IT leaders achieving success in a changing world? To find out, Deloitte and Workday surveyed...

Guide to Strengthening Mainframe Security
Successful phishing attacks lead to a loss of control over user IDs, passwords and credentials. Bad actors...

Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


