Endpoint Security

Zero-trust Solutions for Comprehensive Visibility and Control
Zero-trust solutions exist for nearly every part of the network. However, a piecemeal approach can leave...

The Total Economic Impact™ Of VMware Carbon Black Cloud
Security and IT teams today are constantly dealing with overly complex and siloed toolsets that can't...

Accelerating Digital Transformation through Hyper-Converged Solutions
How can organizations simplify IT in order to improve business agility, enhance financial return on investment,...

The CISO’s Guide to Effective Zero-trust Access
Best practices in network access stipulate a zero-trust access (ZTA) approach. CISOs looking to implement...

Get Total Endpoint Security with KACE
As an IT professional, you're likely under pressure to manage an increasingly complex environment, while...

The Top 5 Myths of Cloud Security
Hybrid cloud security is a hot topic, especially with the massive growth of public cloud providers like...

Two-Factor Authentication Evaluation Guide
In this guide, you will learn how to evaluate a solution based on: ...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

Redefining Data Loss Prevention
Data doesn't move itself. People—whether they are negligent, compromised or malicious—move data in...
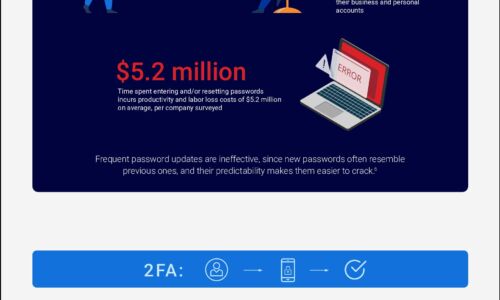
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Cloud networks: Shifting into Hyperdrive
Public cloud is driving digital innovation. As IT organizations around the world continue to radically...

A Buyer’s Guide to Optimizing Remote Employees’ Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

