Endpoint Security

Managing Critical Events with BlackBerry Alert
Every day, organizations face risks from natural, technological, and human-caused critical events. While...

Building the foundation of a mature threat hunting program
Many organizations, especially large global enterprises, don't always have the best visibility into how...

Cloud Security: From Start Point to End Point
Cloud computing offers organisations competitive advantages such as increased speed, agility, scale and...

CMMC Compliance Guide
On January 1, 2020, the United States Department of Defense (DoD) released its Cybersecurity Maturity...

Advance Your Ransomware Defenses
Ransomware isn't new. In fact, it's 30-years-old . What IS new is ransomware's sudden rise as a favored...

Multi-Vector Protection
Educating users is an undeniably effective way to protect them from phishing and other malware, but it...

IT and Cyber Incident Response Communication Templates
BlackBerry® Alert is a critical event management (CEM) solution designed to help organizations prepare...

Automated Endpoint Incident Response: An Enterprise Guide
Strong cybersecurity has always been an essential component of a company's digital transformation success....
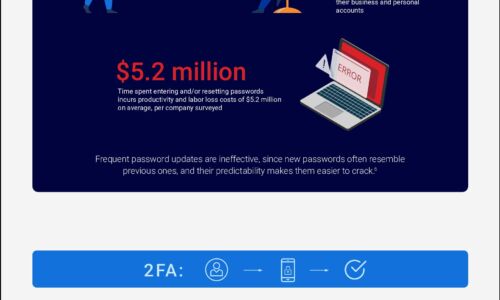
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

3 Ways to Reduce the Risk of Data Loss
Amid the fast-moving digital landscape, security risks are on the rise. People, devices, and objects...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


