Cloud Computing
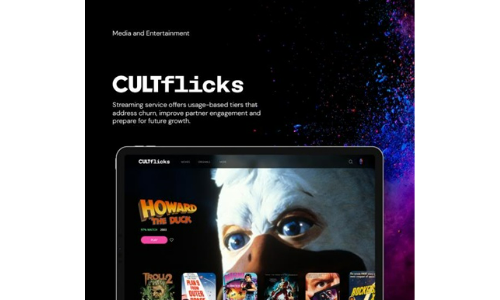
Cultflicks
CULTflicks is a niche video streaming entertainment company that offers the unique experience of specialized...

Enhancing Teams with enterprise-grade telephony
Today's businesses depend on a robust communications experience to drive innovation, and phone calls...

The Book Of Knowledge - Operating Excellence
Customers and employees now demand that enterprises make their operations more responsible, effective...
Box for Banking
Simplify banking for your customers in the cloud I got into banking to push paper and fill out forms....

Optimize Your Network for the Distributed Workforce
Ready. Set. Learn: 8 Ways To Optimize Your Network for Remote Workers. Keeping a distributed workforce...

State of Digital Transformation EMEA 2020
Prior to the pandemic, enterprises were actively migrating private applications to public clouds as well...

5 Best Practices for Securing Modern Web Applications and APIs
Web applications are nothing new. Neither is web application security. Many businesses have been building...

10 Hidden Costs of an On-Premises Phone System (PBX)
Many on-premise phone system (PBX) manufacturers claim that the five-year costs of their systems are...
Would you be ready ....if your employees want to work from Mars?
Midsize companies play a key role in the global economy, driving a large share of job creation, economic...

Unified Fast File and Object (UFFO) Storage
In this book, you get an idea of the vast potential for unstructured data — and also the infrastructure...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



