Applications

The Enterprise Guide to Multi-Cloud
Organizations of all industries and sizes are increasing cloud adoption to meet the demands of today...

High Security 'to Go'
In the wake of digitalisation, the trend towards mobile work practices is also leading to profound changes....

Challenging Times Call for a Cybersecurity Plan of Action
Could there be a more 'exciting' time to be a cybersecurity executive? Some might choose other adjectives:...

Automation for Service Operations
As speed is vital in creating and taking opportunities, you can get ahead by automating the way work...

Modern infrastructure for better end user experiences
Many companies with existing EUC deployments are refreshing their technology stacks to deliver a better...

Advancing SOC Endpoint Incident Response Practices
Even with a comprehensive multi-layered protection solution in place, no organisation can prevent every...
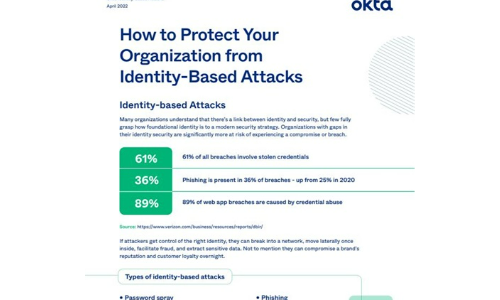
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Speed Up Process Change for SAP ERP
The ability to move fast and having a rapid response to change is needed for businesses to innovate faster....

The Forrester Wave™: Privileged Identity Management
in our 35-criterion evaluation of privileged identity management (PiM) providers, we identified the 11...

Why Today's Business Applications Belong in the Cloud
Has there been a more exciting time to be at the forefront of business? It's unlikely. According to a...

Cyber Attack Trends: Check Point's 2022 Mid-Year Report
The war in Ukraine has dominated the headlines in the first half of 2022 and we can only hope that it...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


