Applications

Unleash the Power of Supplier Data
Today, most big companies have a foggy, disjointed picture of their suppliers. Why? Because their supplier...

Four Ransomware Resiliency Challenges You Can Combat with Confidence
Ransomware is a growing thread to operational resiliency in all digital enterprises. These four stories...

8 Ways that Mobile Scanning can Improve CPG Profitability
This checklist details how CPG manufacturers can identify and address critical supply chain processes....

Use Case - Compliance
IT departments increasingly find themselves spending ever more resources on compliance as laws, regulations,...

Enable End-to-End Zero Trust To Achieve Effective Outcomes
Zero Trust priorities have evolved in 2020 to require solutions that secure your remote workforce with...
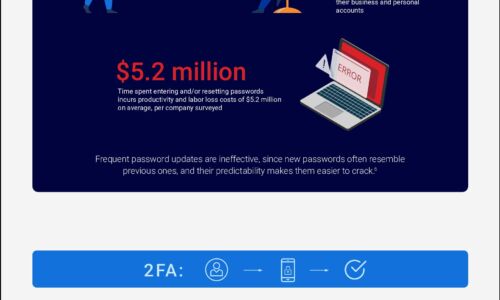
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

Manufacturers get industrial strength security with private 5G.
5G technology has quickly evolved from aspirational to businessready, and many organizations are already...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






