Storage

The New Retail Model: A Four-Step Guide to True Algorithmic Retailing
There is one thing successful retailers have in common, particularly in these uncertain times: a firm...

Centralized Content Access Helps Unify Dispersed Teams
Committing to One Philosophy MandC Saatchi was formed in 1995 by brothers Maurice and Charles Saatchi....

5G for Dummies
5G, the next iteration of wireless networks, is not merely an incremental increase in network speed and...

Migration 8 Best Practices
Deliver cloud value faster with 8 Best Practices to Make Your Cloud Migration a Success. Thousands of...
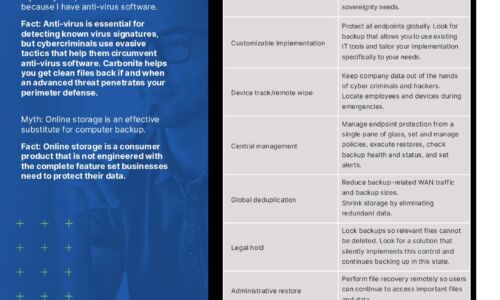
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

Multi-Cloud IT Executive Buyer’s Guide
Intentionally establishing a multi-cloud strategy is a powerful way to modernize your IT infrastructure...

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

Empower End-Users With Better Experiences
Why is end-user computing innovation important? You have a lot of market forces driving your organization,...

The Five Nastiest Security Mistakes Exposing Public Cloud Infrastructure
Public cloud infrastructure has become a critical asset to enterprises that compete on innovation. Protecting...

Evolution Of The Marketer's Toolkit
More than ever, enterprise organisations need a 360-degree view of their customers to deliver the kind...

A Modern Approach to Endpoint Remediation
Even with a comprehensive multi-layered protection solution in place, no organization can prevent every...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

