Server

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...

DDoS attack trends for Q2 2021
Cloudflare's network protects approximately 25 million Internet properties, giving us deep insight into...

DDoS Threat Landscape Report: DDoS Trends from Q3 2022
DDoS attacks are growing larger, stronger, and more sophisticated. In Q3'22, we observed a resurgence...

2021 Technology Industry Cyber Threat Landscape Report
The technology industry is a top target for both cybercriminals and state-sponsored cyber espionage groups....
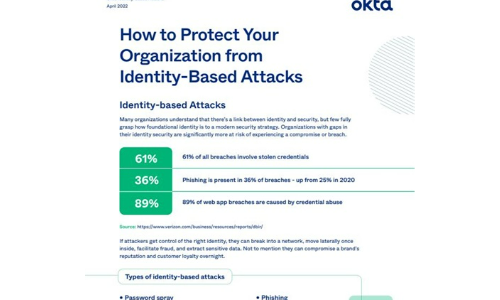
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

The Beginner's Guide to Dynamic Case Management
What is dynamic case management? Who is using it and how can it help you prepare for the future of work? The...

Cybersecurity for the Modern Era
The book explores how cyber attacks and compliance issues are evolving and outlines how you can create...

Future Ready with SaaS Management Guide
For today's modern IT organizations, applications are driving both digital transformation and business...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





