Security Solutions

Edge Computing in Telco Networks: Gaining the Competitive Edge
Earlier this year, Wind River® teamed up with F5, Schneider Electric, and Heavy Reading on a global...

OWASP Top 10
The nonprofit Open Web Application Security Project (OWASP) works to improve the security of software,...

Insider Threat Prevention Guide
In a perfect world, trust would never be violated. Cyber defenses would be impregnable. No employee would...

The Future of Network Security: EMEA
IT and security leaders face a transforming digital world. In order to meet the needs of an evolving...

A Guide To Implementing a Secure SAP System with Fortinet
With today's rapidly changing market conditions and economic climate, organizations are using enterprise...

Protect your organization from ransomware
Get a glimpse of the criminal players who operate within the underground ransomware economy. We'll help...

What the Heck is IAST?
In this eBook, you will learn what IAST is and why it's much different than the previously well-known...

How Malware Can Steal Your Data
As applications drive business, more and more valuable data is accessed and exchanged through them. Cybercriminals...
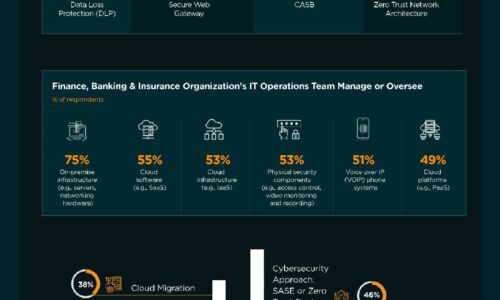
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Security Operations Maturity Model
A practical guide to assessing and improving the maturity of your security operations through Threat...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

