Security Management

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....

Modernize Endpoint Protection and Leave Your Legacy Challenges Behind
2020 was an unprecedented year for security teams amid the global health crisis. The threat landscape...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

Managing Critical Events with BlackBerry Alert
Every day, organizations face risks from natural, technological, and human-caused critical events. While...

Cloud Security Automation For Dummies®
Get the big picture on cloud security, in all its complexity, speed, and scale. Our Cloud Security Automation...

Security Starts Here: Privileged Access Management
The threat of a security incident or critical error is very real, and it's something that auditors are...

Modern upgrade opportunities powered by Veeam DataLabs
With the upcoming end of life of Microsoft Windows server 2008 R2, organizations need to have a plan...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...

Designing Hyper-Aware Industrial Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...

Introducing the Sotero Data Security Platform
IT security professionals continue to struggle with managing countless security solutions and disparate...
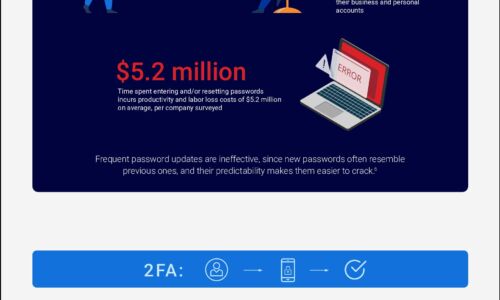
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

