Security Management

Cloud Security Generation Z
Also known as the 'Cloud Generation,' this Generation Z is already reshaping IT…and careers. Many are...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

The Survivor's Guide to Building an Office 365 Network
A Microsoft Office 365 deployment can be daunting. From a fast user experience, to a cost-cutting productivity...

Best Practice Makes Perfect: Malware Response in The New Normal
Before Covid-19, cyber security teams already confessed to being overworked – as high-profile security...

Multi-cloud Load Balancing for Dummies
Legacy hardware-based load balancers don't meet modern enterprise application delivery requirements in...

Top 3 Challenges Your Team Faces When Building in the Cloud
Today's cloud and security teams are asked to do more with less. Although the capabilities and cost of...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Securing Privileged Accounts: Three Steps to Maximize Protection with MFA
Hackers are eyeing your privileged accounts, so you better be using more than 'admin123' to secure them. Multi-factor...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...
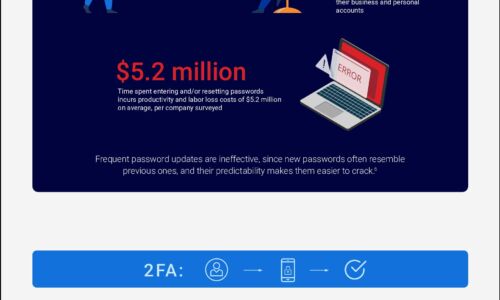
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

The New Reality: Bring Order To Chaos With Unified Endpoint Security
Chaos and confusion dominated the enterprise cybersecurity landscape even before the COVID-19 pandemic...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


