SAN

The State of Threat Prevention: Evasive threats take Center Stage
Digital transformation has rendered many traditional security solutions useless in the face of modern...

Toad for Oracle Tips and Tricks
Toad® for Oracle has been the IT community's tool of choice for more than a decade. With Toad, you are...

Key Storage Considerations in Determining Optimal Workload Placement
In early 2020, IDC performed in-depth primary research on how organizations determine workload placement...

The Mimecast-Netskope-CrowdStrike Triple Play
Security and IT organizations must protect against new attacks at scale — and safeguard data in use,...

2021 State of Malware Report
The story of 2020 is of the devastating COVID-19 pandemic, and of how the world adapted. The story of...

Secure Access Service Edge Palo Alto Networks SASE Comparative Report
This comparative test was commissioned by Palo Alto Networks to evaluate the security efficacy of leading...

Inside The Mind of a Hacker 2019
The first step in cybersecurity? Think like a hacker. According to a recent report, 71% of cybercriminals...

7 trainable soft skills for outstanding agents
The average contact centre manager spends 35% of their time looking for coaching opportunities, but only...

Activate ESG Use Case Guide
Incorporating robust ESG practices into business strategy and execution is critical, not only to be a...

Spotlight: The State of the UK and Ireland Mid-Sized Business and IT
Medium-sized businesses are central to our economies, but this varied market is hard to analyse. So,...
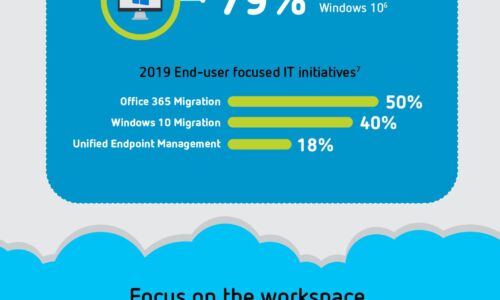
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Next-Gen iPaaS For Dummies
Digital Transformation changes expectations: better service, faster delivery, with less cost. Businesses...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

