SAN

Solving the Key Challenges in Mobile App Development Lifecycle
In a heavily fragmented mobile environment, developing applications compatible with multiple platforms...

2022 Social Engineering Report
In our latest social engineering report, Proofpoint researchers analyse key trends and behaviours in...

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...

The Three Keys to Secure and Successful Cloud Migrations
To make cloud transformations as efficient and successful as possible, companies must remain secure and...

CISO’s Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

A Guide To Implementing a Secure SAP System with Fortinet
With today's rapidly changing market conditions and economic climate, organizations are using enterprise...

Fixing Failed Deliveries
Loqate have surveyed over 3,000 global consumers and 300 retail executives to bring you their latest...

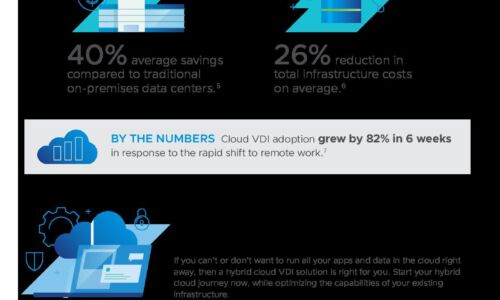
Modern infrastructure for better end user experiences
Many companies with existing EUC deployments are refreshing their technology stacks to deliver a better...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.