NAS

Deliver a CMDB with true business value: 6 essential steps
Your Configuration Management Database (CMDB) provides accurate and reliable information about digital...

A CIO's Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

Isolated Castles: Incident Response in the New Work From Home Economy
Since the shift to work from home, there's been a paradigm shift in the IT and security industry. The...

2022 State of the Threat: A Year in Review
In 2022, ransomware remained the most prevalent form of attack. In investigations by Secureworks® incident...
Web Messaging: What It Is, How It Works, and Why It Matters
As web experiences have become richer and more targeted over the years, there's been a persistent gap...

Reimagining Email Security
In the changing landscape, security and risk management leaders must ensure that existing security solutions...

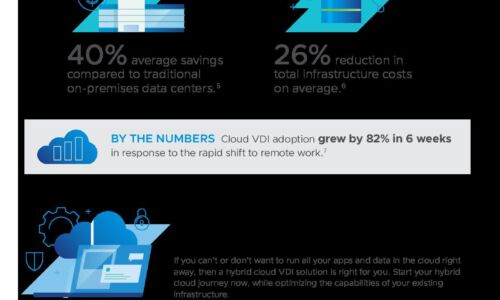
Moor Insights: Cloud is Built on Modern Infrastructure
The modern enterprise lives in a multi-cloud world, where delivery of infrastructure resources and IT...

The Impact of Moving to Independent, Third-Party Software Support
When organizations consider the amount of their IT budget that is spent on yearly maintenance, many focus...

Creative Trends 2022
The seriousness of life during the pandemic has taken its toll. Tired of the mundane and familiar, people...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.