Malware

Cloud Security Automation For Dummies®
Get the big picture on cloud security, in all its complexity, speed, and scale. Our Cloud Security Automation...
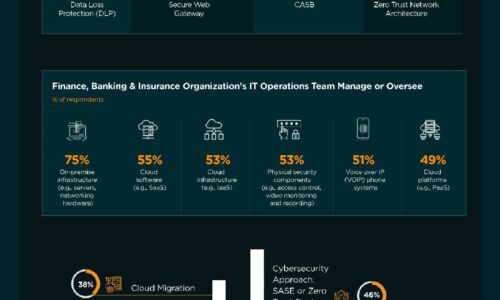
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

The State Of Email Security Report 2019
As cybercriminals continue to use email as a primary vehicle to steal data and deliver advanced threats,...

Four Keys to Navigating the Hardware Security Journey
Ensuring enterprise-wide device security requires a shield, or security posture, that follows and protects...

The Perfect Storm: Why MDR is Your Only Option in Modern Cybersecurity
Covid, work from home, and bring-your-own-device have expanded our threat envelopes 1000X. Attacks with...

Compromise Assessment Use Cases
With cyber attacks increasing both in quantity and sophistication, how can an organization know with...
Don’t Diverge—Converge
Digital acceleration is driving the adoption of hybrid IT architectures. These new hybrid environments...

Global Threat Landscape Report
Another half-year through unprecedented times has passed. But as unique as these times may feel, we continue...

You Got Phished, Now What?
Security leaders work hard to prevent successful phishing attacks. But, despite email security solutions...

Why network security matters in healthcare.
The healthcare sector is an attractive target for cyber criminals — it's a honey pot of highly sensitive...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



