Log Management

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

Centralised Control Simplifies Management, Boosts Security
Aquila Heywood wanted to update its privileged access management processes to increase data security...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...
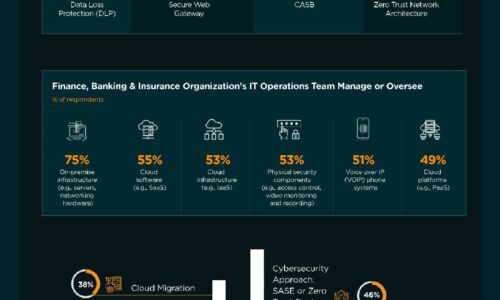
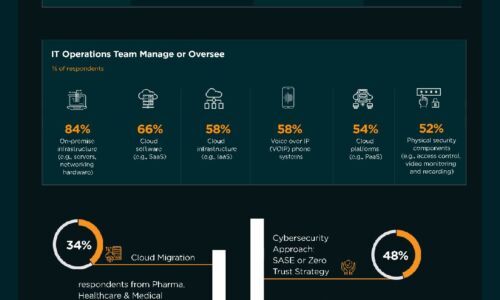
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...

Moving Endpoint Security to Predictive Cloud
Endpoint security is broken. Traditional antivirus (AV) vendors aren't keeping up with today's threats....

Assessing Network Traffic Analysis (NTA) Requirements
Many organizations are struggling to detect, hunt, investigate, and respond to threats in an efficient...

Shift your Web Security to the Cloud, for the Cloud
As enterprises embrace digital transformation, the adoption of software-as-a-service (SaaS) is robust...

Kubernetes on vSphere For Dummies
Discover how building and running containerized applications with Kubernetes on vSphere drives business...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.