IT Threats & Vulnerabilities

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...

32 Security Experts on Changing Endpoint Security
For many companies, the modern business environment has become a mobile workplace in which employees...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

Case Study - Malwarebytes Endpoint Protection and Response
Malwarebytes cut potential downtime to a matter of hours rather than weeks. Malwarebytes complements...
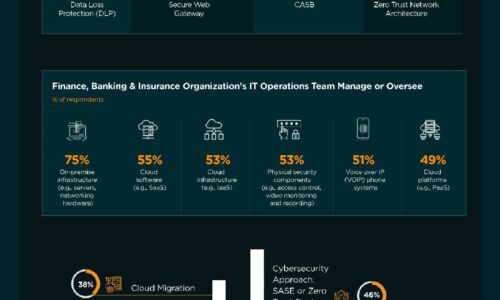
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

10 Endpoint Security Problems Solved By The Cloud Infrographic
The three challenges you're likely facing – cost and complexity, defenses that can't keep up, and overburdened...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...

Why automation is essential for cyber resilience
Digital transformation makes today's businesses more productive and more vulnerable to cyberattacks....
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

10 Endpoint Security Problems Solved By The Cloud
Are you experiencing problems with your traditional AV solution? Read the eBook 10 Endpoint Security...

The Case for Secure Communications
The tapping of voice communications has occurred virtually as long as electronic communication has been...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

