Internet of Things (IoT)

Defend Yourself Against Ransomware and Other Types of Malware
The May 7, 2021, ransomware attack on U.S. fuel network Colonial Pipeline left millions afraid they couldn't...

Core connectivity as a key enabler for smart cities
With urbanisation continuing at breakneck speed around the world, governments need solutions to make...

Reduce Alert Fatigue in Your IT Environment
Security teams are tasked with managing a huge volume of alert logs, and this noise can overwhelm any...

How To Choose a Managed Extended Detection and Response Solution
Organizations face major cybersecurity hurdles. The first challenge is finding effective cybersecurity...

The Future of Government Operations Depends on Digital Transformation
New technologies can help government organizations reduce costs, improve constituent services, and quickly...

The Gorilla Guide to Achieving IT Asset Management Success
ITAM is about knowing what you've got, where it is, who's using it and how much it costs. If you want...

Empowering Medical Manufacturers to Become Leaders
Due to increasing technology and product complexity, regulatory requirements and supply chain issues,...

Reinvention Starts with Cloud Migration of Data Infrastructure
Take the complexity out of your data infrastructure For organizations running legacy data infrastructure...

The Ultimate Guide to Cyber Hygiene
It's critical for organizations to deeply understand their risk posture and have tools in place that...
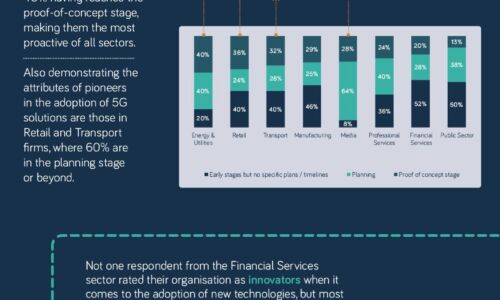
The 5G opportunity within UK industry
Neos Networks research shows that two thirds of organisations expect to have made significant investment...

Data Storage Considerations for Security Analytics
Log analytics has taken increasing importance over the years. In particular, applications that use log...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


