Firewall

Top 3 Challenges Your Team Faces When Building in the Cloud
Today's cloud and security teams are asked to do more with less. Although the capabilities and cost of...
Choose the WAF That's Right for You
Despite the industry's best efforts to bolster secure application development practices, the growing...

The Current State of Zero Trust in the United Kingdom
Zero Trust is a foundational component to digital security and businesses in the United Kingdom are taking...
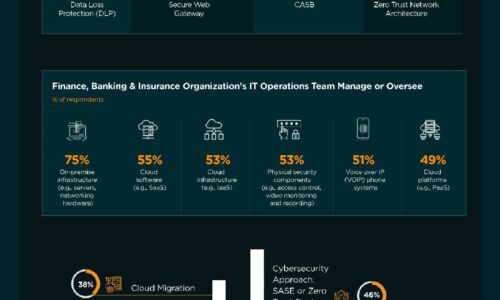
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...

Reduce Alert Fatigue in Your IT Environment
Security teams are tasked with managing a huge volume of alert logs, and this noise can overwhelm any...

2021 Email Threat Report: It Started Out With a Phish
Our 2021 Email Threat Report analyzes the top threats seen over a period of a year across organizations...

An Identity-First Strategy for IT Modernization
The modernisation of IT has become an exercise in doing more with less. IT teams know they need to streamline...

Why Traditional EDR Is Not Working—and What to Do About It
If you work in infosec and haven't been living under a rock, you have undoubtedly heard of EDR. EDR,...

Application Protection Report 2022: In Expectation of Exfiltration
Welcome to F5 Labs' Application Protection Report 2022. As in years past, the goal of this report is...

Collective Defense: A radar-like view of cyber threats
IronNet is committed to answering the World Economic Forum's call to action for collaborative cyber defense....

Setting up IT for Success
Every decade or so, we've seen the technology market undergo major shifts. Over the past few decades,...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

