Firewall

5 ways IT can increase employee productivity with Chrome Browser
As enterprises contine to adopt web-based apps, users spend more time their web browser than ever before. With...

Active Directory Security Primer
The most important question in security is, 'Is our data safe?' If you can't answer that, it's tough...

5 Steps to Secure Your Remote Workforce: a Practical Guide
Even before COVID-19, IT and security professionals knew that working remotely was becoming more popular,...

Protecting the ATM Network with Fortinet
Protecting a network of geographically dispersed automated teller machines (ATMs) is a key challenge...

Open Channels, Hidden Threats
How Communication and Social Media Tools Are Changing the Insider Risk Equation for Compliance, IT and...
Is Your WAF Keeping Pace with Today's Advanced Threats eBook
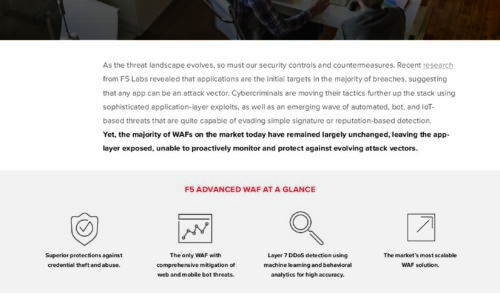
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...
Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Accelerating Adobe Experience Cloud Results
Our digital experience experts can help you devise a strategy to maximize your Adobe solutions and get...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

5 Best Practices for Securing Modern Web Applications and APIs
Web applications are nothing new. Neither is web application security. Many businesses have been building...

Securing financial services network data
Financial services is one of the most tightly regulated business sectors. The FSA, the Data Protection...

KuppingerCole Leadership Compass
Leaders in innovation, product features, and market reach for access governance and intelligence. Delivering...

How Cloudflare Access Replaces a VPN
The rise of remote work has caught many companies off guard. Many organizations have only purchased enough...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
