Embedded Systems

Windows 10 for Dummies, 2nd Edition (Full eBook)
The most comprehensive guide to Windows 10, updated with the latest enhancements. This eBook includes...

The Zero Trust Guide To Remote Worker Security
With the recent increase in the number of employees working from home as a result of the COVID-19 outbreak,...

BlackBerry Guard: Solution Brief
Many businesses overlook or underinvest in managed detection and response (MDR), a critical aspect of...

PHP, MySQL, and JavaScript All-in-One For Dummies
Get the basics on four key web programming tools in one great book! PHP, JavaScript, and HTML5 are essential...
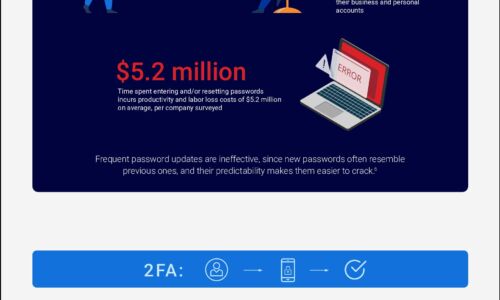
The Trouble with Modern Authentication Approaches
Sensitive data is increasingly being accessed by mobile and dispersed workforces from the cloud, resulting...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...

PHP, MySQL, & JavaScript All-in-One For Dummies
Get the basics on four key web programming tools in one great book! PHP, JavaScript, and HTML5 are essential...

IT and Cyber Incident Response Communication Templates
BlackBerry® Alert is a critical event management (CEM) solution designed to help organizations prepare...

The New Reality: Bring Order To Chaos With Unified Endpoint Security
Chaos and confusion dominated the enterprise cybersecurity landscape even before the COVID-19 pandemic...

Ransomware Prevention and Remediation
The global damage costs of ransomware are projected to reach $20 billion in 2021. This includes not only...

Reduce the cost of running windows workloads by migrating to AWS
Optimise Windows Server, modernise .Net applications and decrease SQL Server licensing costs. Download...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


