Email Security

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Cybersecurity Insiders: Cloud Security Report
The 2019 Cloud Security Report from Cybersecurity Insiders highlights what is and what is not working...

The Hidden Cost of Free M365 Security Features
All email, cloud, and compliance solutions are not created equal. As organisations make the move to Microsoft...

Enable End-to-End Zero Trust To Achieve Effective Outcomes
Zero Trust priorities have evolved in 2020 to require solutions that secure your remote workforce with...

Driving Real Behaviour Change
Today's most potent cyber threat isn't a zero-day vulnerability, new malware or the latest exploit kit....

A study of employee cybersecurity awareness in the Middle East
The cyber threat landscape in the Middle East is rapidly evolving, with cybercriminals increasingly targeting...

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

The Complete Guide to Enterprise Ransomware Protection
The SentinelOne Complete Ransomware Guide will help you understand, plan for, respond to and protect...
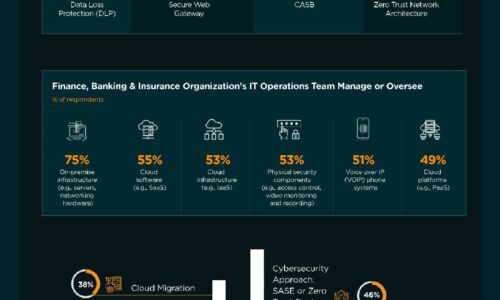
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Part Three- Futureproofing your cybersecurity strategy
A VIP or executive impersonation attack occurs when a bad actor poses as a trusted leader within an organization....

Secure Beyond Breach
Securing the perimeter is no longer enough. The focus has shifted to ensuring your organization continues...

Threat Spotlight: Protecting your business in 2022
Cybersecurity threats are rapidly evolving. In the latest attacks, cybercriminals are using a range of...

Dissecting a Cloud Attack: Securing Azure with AzLog
Microsoft Azure is one of the fastest-growing cloud infrastructure services. Unfortunately, the advantages...

The Forrester Wave™: Enterprise Email Security, Q2 2021
In a 25-criterion evaluation of enterprise email security providers, Forrester identified the 15 most...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.