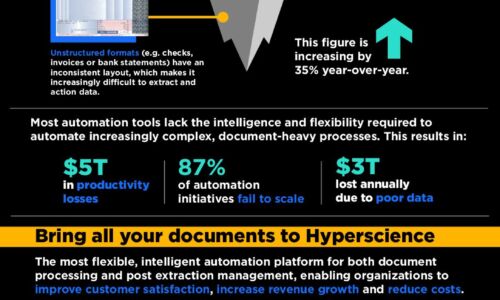
AIM

Rebellions and rejections report
The global pandemic forced organizations to pivot rapidly from an office-based workforce model to one...

State Of Software Security Report 2019
The 2019 Veracode State of Software Security report represents the 10th version of the report. Much like...

The Gorilla Guide to Rapid Restores with Flash and Cloud
Welcome to this Gorilla Guide covering enterprise data protection, backup, and recovery. The purpose...
Streamline Your Cloud Operations with Slack and AWS Chatbot
CloudOps professionals—from DevOps engineers to site reliability engineering (SRE) teams—pursue paths...

Simplified Zero Trust Segmentation with Illumio Core
Modern ransomware is one of the most significant cybersecurity threats to critical services, compute...

VMware Multi-Cloud Architecture - Enabling Choice & Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

Three reasons your cloud data warehouse needs cloud analytics now
Getting more data into the hands of more users across organisations is a challenge many data leaders...

High Security 'to Go'
In the wake of digitalisation, the trend towards mobile work practices is also leading to profound changes....
G2 community reviews ServiceNow App Engine
It's clear that rapidly building custom apps is vital for creating and taking opportunities for growth....

Advancing SOC Endpoint Incident Response Practices
Even with a comprehensive multi-layered protection solution in place, no organisation can prevent every...

Your Path to Cloud Analytics: 10 Key Considerations
Now more than ever, businesses are choosing SaaS for modern analytics. That's because today's vastly...
Sign up for FinTech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.